SonicWall announced new platform offerings and enhancements for small, mid-sized and distributed businesses and enterprises to protect against targeted attacks on wireless networks, cloud apps and endpoints. In addition to a new line of firewalls designed to consolidate security, networking and performance, SonicWall introduced new cloud-managed Wi-Fi access points and wireless planning tools designed to ease the deployment of global wireless networks.
The company also provides real-time protection for cloud applications, including Office 365, G Suite, Box and Dropbox, in addition to equipping organizations with advanced Endpoint Detection and Response (EDR) capabilities.
“Cybercriminals take advantage of unintentional gaps left in the security architecture fabric,” said SonicWall President and CEO Bill Conner. “SonicWall’s core mission is to empower organizations to improve their security posture and better protect against growing vulnerabilities. As our platform evolves, expands and integrates, we continue to deliver proven security solutions to organizations looking to enhance visibility, streamline processes and implement cost efficiencies.”
Seamlessly plan, secure expanding wireless networks
To enhance wireless security and performance for SMBs and distributed enterprises, SonicWall delivers a range of new cloud-based deployment and management solutions.
SonicWall WiFi Cloud Manager and SonicWiFi mobile app simplify wireless access, control and troubleshooting capabilities across networks of any size or region, with single sign-on (SSO) access provided by the cloud-based Capture Security Center to ensure proper security measures are taken.
Provisioning new wireless hardware can often be time-consuming when taking adequate measures to ensure employees receive secure, high-performance wireless connectivity. Pairing SonicWall WiFi Cloud Manager with SonicWall Zero-Touch Deployment and wireless mesh networking allows wireless expansion to be accomplished within minutes.
With Capture Security Center, administrators can also leverage the intuitive, easy-to-use SonicWall WiFi Planner surveying capabilities to design and deploy secure wireless networks that enhance the user experience and ensure workforce productivity.
“Deploying a secure wireless network is no longer an option, it’s a requirement,” said James Crifasi, Vice President and Chief Technology Officer at RedZone Technologies. “SonicWall wireless tools have proved to be lower in cost and reduce the need for complex overlay management systems. We are thrilled at the improvements in security, management, and performance the new series has given us.”
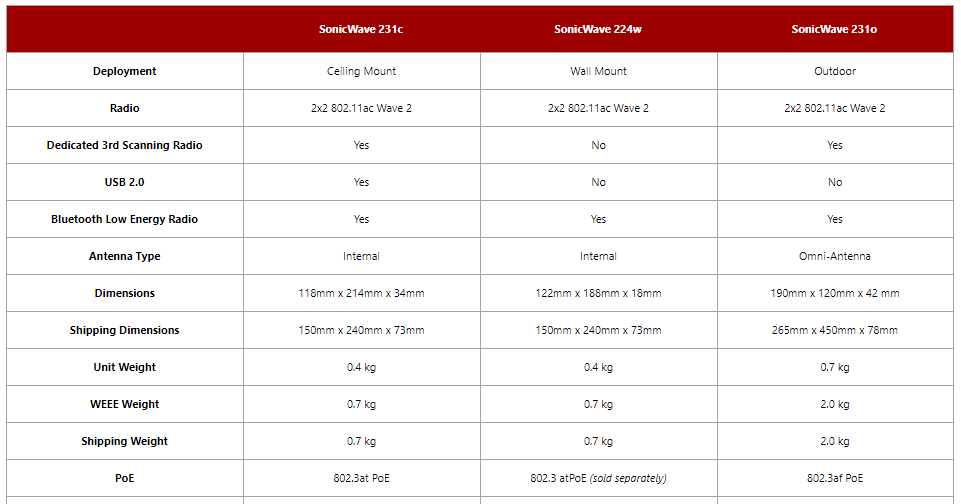
Organizations can pair new SonicWave access points with SonicWall firewalls for high-speed 802.11ac Wave 2 wireless access and deep packet inspection (DPI) of encrypted and unencrypted traffic. These new access points can also be deployed securely without a SonicWall firewall and offer integrated security services, including the Capture Advanced Threat Protection (ATP) sandbox service and SonicWall Content Filtering Service.
New cost-effective firewalls consolidate security, networking, performance
IT managers need a solution that solves their security, connectivity and performance concerns in a small form factor appliance at a price point within their budget.
SonicWall’s new SOHO 250 and TZ350 series firewalls provide a unified security solution at a low total cost of ownership. Designed for small, mid-sized and distributed enterprise organizations with remote locations, the SOHO 250 and TZ350 integrate essential networking features and industry-validated high-security effectiveness to protect data and connected devices, including IoT.
The new firewall range combines high-speed threat prevention and software-defined wide area networking (SD-WAN) technology with an extensive range of networking and wireless features, plus simplified deployment and centralized management capabilities.
SonicWall Secure SD-WAN technology reduces costs by replacing expensive MPLS technology with lower-cost internet access. Deploying SOHO 250 and TZ350 firewalls is greatly simplified with SonicWall Zero-Touch Deployment, a key component of SonicWall’s cloud-based Capture Security Center.
Secure business-critical data in cloud applications
Cloud applications are vital to organizations’ production, sales and communications, and are increasingly the target of attacks. To thwart never-before-seen malware variants, targeted phishing attacks, account takeover due to compromised credentials and data loss, SonicWall Cloud App Security 2.0 provides real-time protection for business-critical SaaS apps, including Microsoft Office 365, G Suite, Box and Dropbox.
“When organizations move to the cloud or SaaS applications, their sensitive data moves into shared infrastructure and the traditional perimeter evaporates,” said Jeff Wilson, Senior Research Director, Cybersecurity Technology at IHS Markit. “Administrators need to have the same complete visibility and access control inside their networks and in the cloud, and they need to be able to control security and enforce strong threat and data loss protection with policies that keep risk and compliance in mind. Organizations should look for a Cloud Access Security Broker (CASB) solution that provides easy deployment, granular control and has zero impact on the user experience.”
To identify and mitigate malicious malware or files stored in SaaS solutions, such as OneDrive and SharePoint, SonicWall Cloud App Security 2.0 integrates with the Capture ATP sandbox service, which includes patent-pending Real-Time Deep Memory Inspection (RTDMI) technology. The new features extend SonicWall real-time automated breach detection and prevention capabilities into sanctioned SaaS environments using API integrations and monitor user-to-cloud and cloud-to-cloud traffic to identify unapproved cloud applications.
Email is the most common threat vector and security controls must be adapted as organizations move to cloud email, such as Exchange Online with Office 365 or Gmail with G Suite. To combat advanced targeted phishing attacks, Cloud App Security 2.0 includes machine-learning anti-phishing capabilities that are trained to catch malicious emails missed by the built-in security controls of cloud email platforms.
Empowering administrators with advanced endpoint detection and response
Designed to increase administrators’ response time, visibility and insight into advanced threats, SonicWall Capture Client 2.0 gives organizations active control of endpoint health with advanced endpoint detection and response (EDR) capabilities.
Administrators have the ability to track threat origins and intended destination, kill and quarantine as necessary and roll back endpoints to a last-known healthy state in the event of an infection.
External USB devices can pose a serious threat to network security, potentially delivering malware, ransomware and viruses to vulnerable endpoints. SonicWall’s new Capture Client feature, Device Control, helps organizations reduce their attack surface by locking out unknown or suspicious devices.
Security policies can easily be created to whitelist clean devices, such as printers and removable storage, and narrow the threat plane. Unlike legacy antivirus solutions, systems no longer have to be taken offline to conduct forensic analysis and/or reimaging when mitigating malware or cleaning endpoints.
Employee behavior can prove challenging when building a sound cybersecurity defense. By using SonicWall Content Filtering Service capabilities, Capture Client blocks access to millions of known malicious domains, IP addresses and botnets to prevent infections caused by employee error or curiosity.